Internet Of Things Cybersecurity Concept Circuit Board With Hacker And Computer Code On Cpu 3D Illustration Stock Photo, Picture and Royalty Free Image. Image 80333765.

Set Computer Monitor Screen, Hacker Coder, System Bug, Processor with Microcircuits CPU, Programming Language Syntax Stock Vector - Illustration of development, vector: 228526125

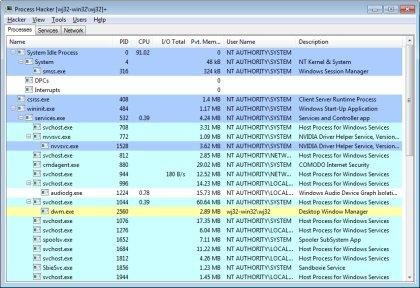
CrossTalk - Another Intel-Exclusive Vulnerability Worries Security Researchers | Cyware Alerts - Hacker News

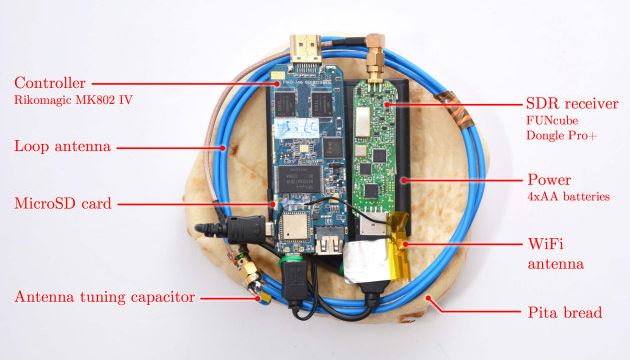
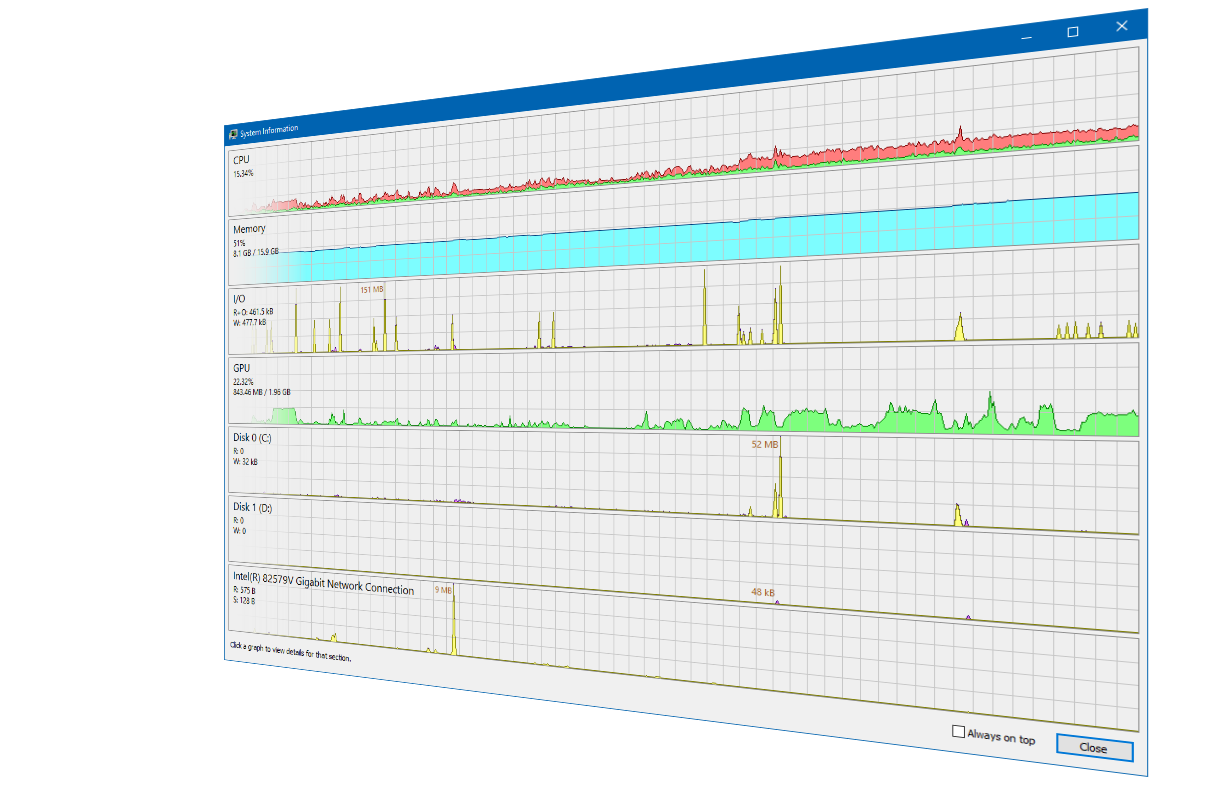
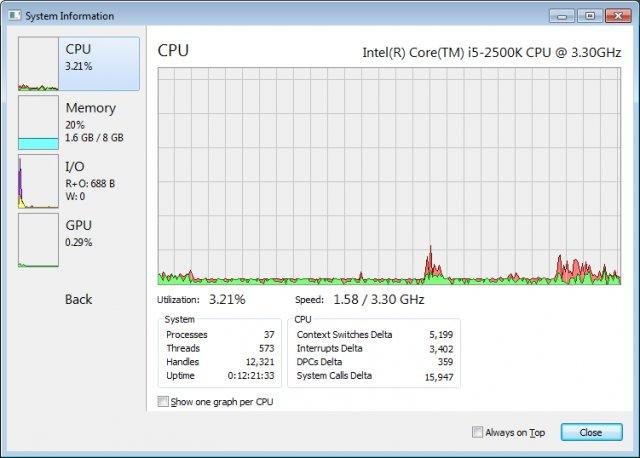
World's best 500+ cybersecurity experts fail to hack the Morpheus processor - NotebookCheck.net News

M1 processor chip. Network digital technology with computer cpu chip on dark motherboard background. Protect personal data and privacy from hacker cyberattack. Stock Photo | Adobe Stock